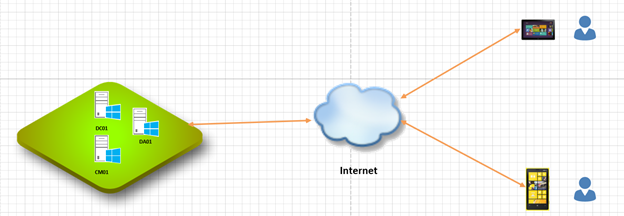
Our client is looking to methods of remote access. As such we have been engaged to provide a DirectAccess 2016.
DirectAccess provides users with the experience of being seamlessly connected to their intranet any time they have Internet access. When DirectAccess is enabled, requests for intranet resources (such as email servers, shared folders, or intranet websites) are securely directed to the intranet, without the need for users to connect to a VPN. DirectAccess enables increased productivity for a mobile workforce by offering the same connectivity experience both inside and outside of the office. This document also can be used for DirectAccess 2012R2.
 Note NoteDo not attempt to deploy Remote Access on a virtual machine (VM) in Microsoft Azure. Using Remote Access in Microsoft Azure is not supported. You cannot use Remote Access in an Azure VM to deploy VPN, DirectAccess, or any other Remote Access feature in Windows Server 2016 or earlier versions of Windows Server. For more information, see Microsoft server software support for Microsoft Azure virtual machines. |
Let’s follow the steps to build DirectAcess.
Create a Security Group for Direct Access Clients
- Log on to DC Server.
- From the Start screen, click Administrative Tools.
- Click Active Directory Users and Computers.
- In the console tree, click the arrow to expand domain (local), and then click Users.
- In the Tasks pane, click New, and then click Group.
- In the Create Group dialog, type DirectAccessClients for Group name.
- Scroll down to access the Members section of the Create Group dialog, and click Add.
- Click Object Types, select Computers, and click OK.
- Add the computer name of Direct Access Clients, and then click OK.
- In the Tasks pane, click New, and then click Group.
- In the Create Group dialog, type DirectAccessManagement for Group name.
- Scroll down to access the Members section of the Create Group dialog, and click Add.
- Click Object Types, select Computers, and click OK.
- Add the computer name of Direct Access Management Workstations, and then click OK.
- Close Active Directory Users and Computers console.
Create the network location server DNS record
- Log on to DC Server.
- From the Start screen, click Administrative Tools.
- Expand DC, Forward Lookup Zones, and select the local domain name.
- Right-click the local domain name, and then click New Host (A or AAAA).
- Under Name, type DirectAccess-NLS, and under IP address, type IP address of Direct Access Server.
- Click Add Host, click OK, and then click Done.
- Right-click the local domain name, and then click New Host (A or AAAA).
- Under Name, type DirectAccess-ISATAP, and under IP address, type IP address of Direct Access Server.
- Click Add Host, click OK, and then click Done.
- Close the DNS Manager console.
Configure Group Policy for DirectAccess Client firewall rules
- Log on to DC Server.
- From the Start screen, click Group Policy Management.
- In the console tree, expand Forest: domain.local\Domains\local domain name.
- Rick-click DirectAccess Workstations OU, and select Create a GPO in the domain, and Link it here.
- Assign the name DirectAccess WFAS Settings to the new group policy.
- Expand the DirectAccess Workstations OU, click the name DirectAccess WFAS Settings policy.
- On Scope tab, add the DirectAccessClients group to Security Filtering and remove the default group.
- On Details tab, set the GPO Status to User configuration settings disabled.
- Right-click the name DirectAccess WFAS Settings policy, and select Edit.
- In the console tree of the Group Policy Management Editor, expand Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Windows Firewall with Advanced Security-LDAP://CN=….
- In the console tree, select Inbound Rules, right-click Inbound Rules, and then click New Rule.
- In the New Inbound Rule Wizard, on the Rule Type page, click Custom, and then click Next.
- On the Program page, click Next.
- On the Protocols and Ports page, in Protocol type, click ICMPv4, and then click Customize.
- On the Customize ICMP Settings dialog box, click Specific ICMP types, select Echo Request, click OK, and then click Next.
- Click Next three times.
- On the Name page, in Name, type Inbound ICMPv4 Echo Requests, and then click Finish.
- In the console tree, right-click Inbound Rules, and then click New Rule.
- On the Rule Type page, click Custom, and then click Next.
- On the Program page, click Next.
- On the Protocols and Ports page, in Protocol type, click ICMPv6, and then click Customize.
- On the Customize ICMP Settings dialog box, click Specific ICMP types, select Echo Request, click OK, and then click Next.
- Click Next three times.
- On the Name page, in Name, type Inbound ICMPv6 Echo Requests, and then click Finish.
- In the console tree, right-click Inbound Rules, and then click New Rule.
- On the Rule Type page, click Port, and then click Next.
- On the Protocol and Ports, select TCP and type 3389 in Specific local ports.
- Click Next three times.
- On the Name page, in Name, type Inbound RDP Requests, and then click Finish.
- In the console tree, right-click Inbound Rules, and then click New Rule.
- On the Rule Type page, click Port, and then click Next.
- On the Protocol and Ports, select TCP and type 445 in Specific local ports.
- Click Next three times.
- On the Name page, in Name, type Inbound File Access Requests, and then click Finish.
- Right-click Inbound ICMPv4 Echo Requests, select Properties.
- On the Advanced tab, change the Edge traversal drop-down menu to Allow edge traversal, and then click OK.
- Right-click Inbound ICMPv6 Echo Requests, select Properties.
- On the Advanced tab, change the Edge traversal drop-down menu to Allow edge traversal, and then click OK.
- Right-click Inbound RDP Requests, select Properties.
- On the Advanced tab, change the Edge traversal drop-down menu to Allow edge traversal, and then click OK.
- Right-click Inbound File Access Requests, select Properties.
- On the Advanced tab, change the Edge traversal drop-down menu to Allow edge traversal, and then click OK.
- Confirm that the rules you created appear in the Inbound Rules node. Close the Group Policy Management Editor, and close Group Policy Management console.
Configure Group Policy for ISATASP
- Log on to DC Server.
- From the Start screen, click Group Policy Management.
- In the console tree, expand Forest: domain.local\Domains\local domain name.
- Rick-click DirectAccess Workstations OU, and select Create a GPO in the domain, and Link it here.
- Assign the name DirectAccess ISATAP Settings to the new group policy.
- Expand the DirectAccess Workstations OU, click the name DirectAccess ISATAP Settings policy.
- On Scope tab, add the DirectAccessManagement group to Security Filtering and remove the default group.
- On Details tab, set the GPO Status to User configuration settings disabled.
- Right-click the name DirectAccess ISATAP Settings policy, and select Edit.
- In the console tree of the Group Policy Management Editor, Enable the Computer Configuration\Policies\Administrative Templates\Network\TCPIP Settings\IPv6 Transition Technologies\ISATAP Router Name policy.
- Type DirectAccess-ISATAP.domain.local to Enter a Router or relay name.
- Enable the Computer Configuration\Policies\Administrative Templates\Network\TCPIP Settings\IPv6 Transition Technologies\ISATAP State policy.
- Change Select from the following states to Enable State.
- Confirm that the rules you created appear in the Inbound Rules node. Close the Group Policy Management Editor, and close Group Policy Management console.
To be continue……
Cary Sun @SifuSun
