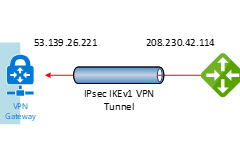
This document will show you how to step by step to configure Cisco Meraki to azure site to site VPN IPsec tunnel IKEv1.
If the Cisco Meraki Security appliances running firmware less than version 15.12 do not have support for IKEv2. Also, there is a bug at concurrent firmware 14.53 (confirmed by Meraki support engineer), when you build up a VPN non-Meraki peer with Azure, the all auto VPN peers will down and won’t come back on line until you reboot the security appliance. Everything will be fine after reboot it.
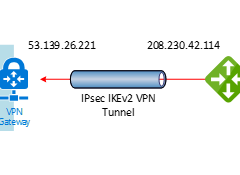
This document will show you how to step by step to configure Cisco Meraki to azure site to site VPN tunnels IKEv2.
The Cisco Meraki Security appliances running firmware must be on firmware 15 or greater to take advantage of IKEv2, because the firmware 15.x is still beta version, you need to ask Meraki support to upgrade it for you if you need it.
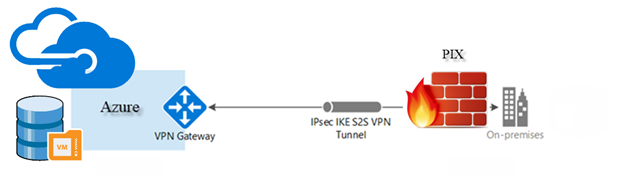
Today, I would like to tell you how to build a site-to-site VPN from Sophos XG firewall to Azure, if you have no budget to buy a hardware base firewall for you home office or lab, no worry, you also can download and install at Microsoft Hyper-V (or others) Virtual Machine and it’s free!!
Today, my customer asked me that is it possible to expand system volume disk space for their Windows Server 2003 virtual machine? The answer is Yes, we can do it without any 3rd party tools. You just need a Windows Server 2008 or up to help this. Let’s follow the step by step to do it.